Over the past few decades, electronic health records, or EHRs, have reduced medical errors and improved clinical decision-making while increasing operational efficiency. With electronic records, healthcare institutions can more easily and quickly gather and disseminate accurate patient data, streamlining operations and cutting expenses.
As digital healthcare records become more widespread, they have become primary targets for cyberattacks and data breaches. Since private medical data is now digital, hackers have more ways to get it, keep it hostage, or steal it for fraud and identity theft.
This growing threat has made healthcare data one of the most valuable targets, increasing the urgency for protective measures. Because of this, businesses have to invest a lot of time and energy in securing healthcare applications and adhering to stringent security and data* privacy laws.
How can your company optimize the use of EHRs to increase productivity and raise the standard of care while safeguarding them better and adhering to legal requirements? You can begin by familiarizing yourself with essential laws and industry standards and get help from application security services. From there, you can formulate a comprehensive strategy to build a resilient EHR system.
The Role of HITECH and HIPAA in Driving EHR Adoption
EHR usage increased quickly after the Health Information Technology for Economic and Clinical Health (HITECH) Act was passed in 2009. The act required that healthcare providers deploy and demonstrate meaningful use of EHRs to preserve their current Medicaid and Medicare reimbursement levels. It also provided incentives for adopting new technology in the healthcare industry.
Besides HITECH, HIPAA also plays a crucial role in ensuring that EHR adoption increases. Stringent guidelines are mentioned to protect patient privacy and sensitive healthcare information.
Before 2009, EHR usage was less than 10% in non-federal acute-care hospitals. By the end of 2021, over 96% of these institutions had implemented electronic health records. Other categories of providers have shown significant changes comparable to those observed in the days of old paper records.
HIPAA compliance further ensures that patient data remains confidential and safeguarded from breaches or unauthorized access as digital records expand.
- The objectives of the HITECH Act are to enhance patient access, promote EHR Adoption, strengthen security and privacy, and improve Healthcare.
Together, HIPAA and HITECH work to secure healthcare systems, ensuring that patient data remains well-protected and secure.
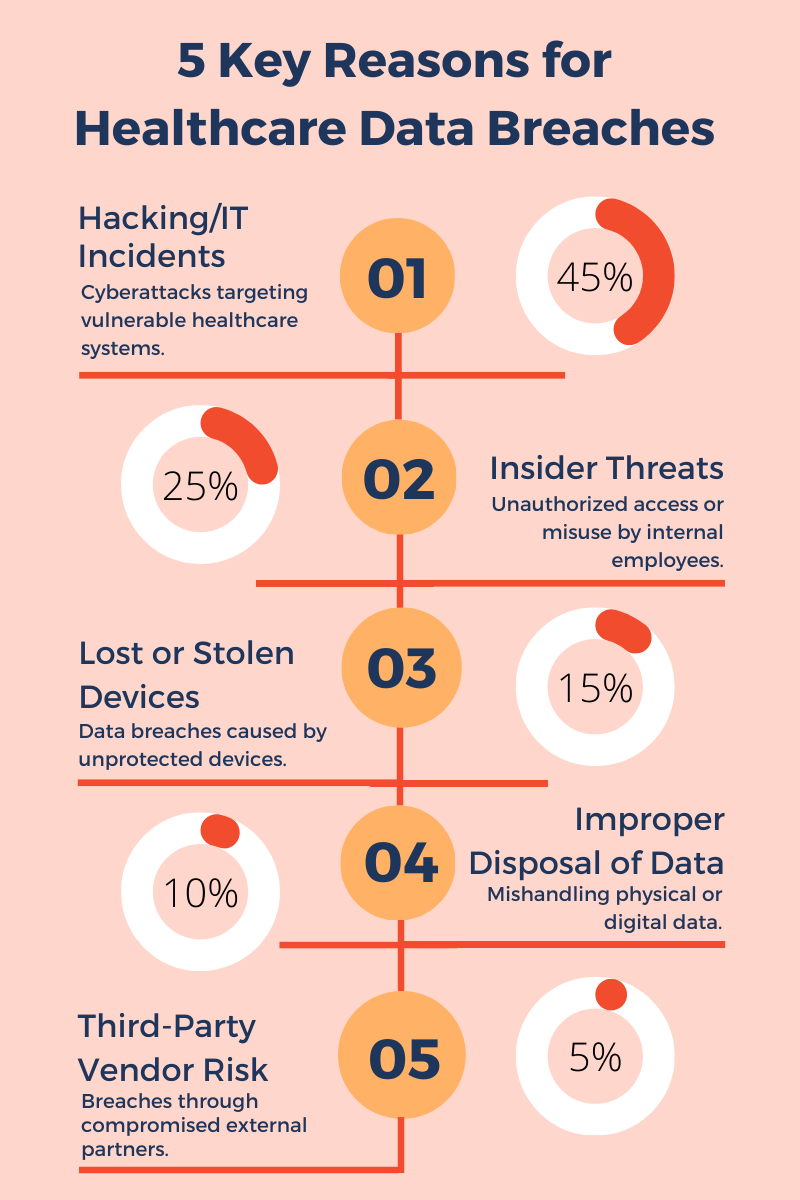
Why are EHR Systems a Prime Target for Cyberattacks?
While electronic health records are becoming the norm for gathering and disseminating patient data, storing sensitive information in an unsecured environment (public Wi-Fi or outdated software) increases the risk of data breaches.
There are several reasons why patient records are compromised or taken:
- Identity theft– Stealing crucial information to build false identities.
For example, Cyberattackers may obtain your social security number and use it for fraudulent accounts or loans in the victim’s name.
- Insurance fraud – Submitting fake claims to insurance companies.
For example, fraudsters might create fake medical records to file claims for treatment or procedures that were never performed.
- Prescription fraud —Obtaining drugs under a patient’s identity.
For example, an identity thief may duplicate a doctor’s prescription to get controlled substances using another person’s name.
- Data stealing on the Dark web– Selling sensitive data on the black market.
Cybercriminals often sell stolen credit card numbers, personal identification details, and login credentials on Dark web forums.
- Phishing scams– Utilizing personal information for making fake emails or phone calls.
For example, attackers may impersonate a bank or legitimate organization and send emails that trick users into revealing sensitive information, like passwords or account numbers.
- Ransom– Requiring hefty payments in exchange for data from a medical facility.
For example, in a ransomware attack, hackers may encrypt a hospital’s patient records and demand payment for the decryption key to restore access.
Massive collection of personal data can be highly lucrative for criminals operating in the black market. In some cases, entire criminal operations are dedicated to identity theft.
How EHR Breaches Equally Harm Healthcare Providers?
The consequences of EHR breaches for healthcare providers are equally damaging.
Among the potential outcomes are the following:
-
Government penalties for breaking privacy regulations.
According to the U.S. Department of Health and Human Services (HHS), penalties for violating HIPAA regulations can reach up to $50,000 per violation, with a maximum annual penalty of $1.5 million.
-
Costs for public relations management and legal counsel.
The average total cost of a data breach in healthcare was $9.23 million, which includes legal fees, public relations efforts, and regulatory fines.
-
Imprisonment in situations involving severe carelessness or complicity.
Under HIPAA, healthcare providers found guilty of knowingly obtaining or disclosing PHI can face criminal charges, with penalties ranging from fines to imprisonment for up to 10 years.
-
Financial disaster brought on by a decline in income and reputation.
Research indicates that 60% of small healthcare businesses close within six months of a data breach due to financial strain.
Cybersecurity consulting services are essential to safeguard ePHI and underpin system security. Security measures have been implemented to protect patient information and electronic health records (EHRs) since their trust and privacy breaches have far-reaching consequences.
How do Application Security Services Help Mitigate Cyberattacks?
Application security services can assist in mitigating cyber threats by utilizing a variety of mechanisms.
Here’s how application security services protect against cyberattacks by identifying vulnerabilities–
-
Runtime Application Self-Protection (RASP)
It assesses user behavior and application traffic to analyze and prevent cyber threats. Additionally, RASP can terminate sessions that have already been exploited and issue alerts.
-
DDoS protection services
They can detect and mitigate attacks in real-time and safeguard against volumetric and application-layer attacks.
-
Encryption
Application security services make data unreadable and unusable, even if a hacker can access it.
-
Data backups
These services allow organizations to restore their information and get back up and running quickly if an attack occurs.
-
Firewalls
It can monitor network traffic and block connection attempts that could hurt your website or application.
Benefits of Application Security Services For EHRs
An increasing number of organizations are seeing the potential advantages of switching to EHR security compliance services, which include:
- More comprehensive records: EHRs facilitate compiling accurate, thorough, and current patient records.
- Increased collaboration: Collaboration across numerous providers is improved because of EHRs.
- Improved Efficiency: Time-consuming, expensive paper-based tasks like physically duplicating papers and photographs and transferring information between providers have been replaced by electronic health records (EHRs). Protecting EHR with security services can also increase the effectiveness of billing and scheduling.
- Fewer errors: More efficient access to comprehensive, current patient information reduces the likelihood that doctors may prescribe medications that could cause harmful allergic responses or interfere with preexisting medical conditions.
- Enhanced patient involvement: By making it easier for patients to receive direct health information, providers may motivate them to take a more active role in their own treatment.
How AppSec Services Safeguard Electronic Health Records?
How can businesses adhere to HIPAA regulations while protecting EHR systems from cyberattacks? The most effective tactics will include several security layers.
-
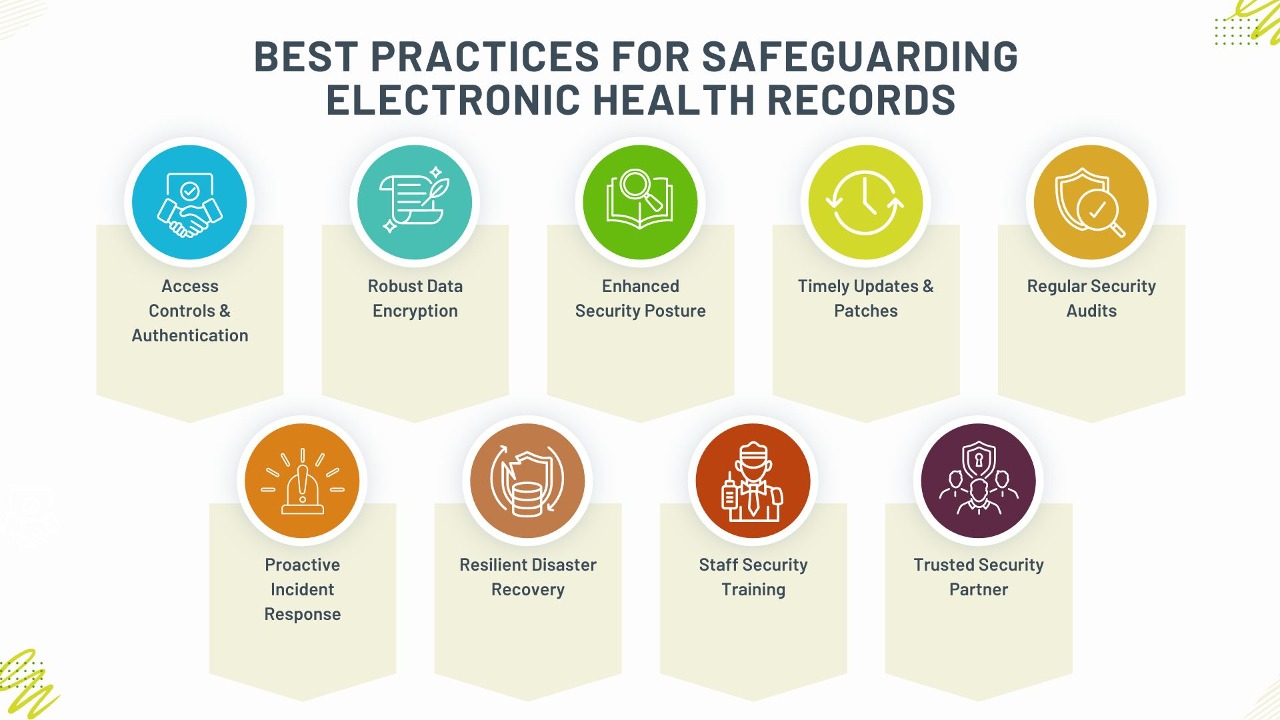
Use Access Controls and Authentication Measures
By implementing role-based access restrictions, you can ensure that users can only access the information necessary to perform their roles. These restrictions can limit unwanted insider access and prevent attackers from having an entire run within your network, even if they obtain an authorized user’s credentials.
Multi-factor authentication (MFA) provides an additional line of protection. By asking users to supplement their passwords with another form of verification, such as a USB key or face recognition, you can prevent hackers from using credentials they have obtained to access EHRs.
-
Implement Robust Data Encryption
Data encryption is another crucial tool for safeguarding application security for healthcare data. Even if hackers obtain critical information, they can be prevented from exploiting it by encrypting data in transit and at rest. Attackers can’t view data without the decryption key.
-
Improve EHR Application Security Posture
Phishing is a common starting point for cyberattacks that target PHI and EHRs. Attackers try to trick people into clicking on links in texts or emails that lead to fake websites. When users provide their login information, criminals can access networks by stealing it. After that, the attackers can infect EHR systems with malware, such as ransomware.
Installing antivirus and anti-malware software can help prevent malware and ransomware from running. Meanwhile, network monitoring tools can help identify malware connections with command-and-control servers, and firewalls can prevent malware from accessing networks.
-
Ensure Security Through Timely System Updates and Patches
Maintaining up-to-date operating systems and apps is crucial for your multi-layered defense plan. EMR/EHR software development providers monitor threat behavior closely and work to find and address product flaws. By wholly and quickly installing updates and patches throughout your IT system, you can lessen the likelihood that hackers will infiltrate your network and compromise EHRs.
-
Conduct Regular Security Audits and Penetration Tests
EHR security calls for ongoing work. You must ensure that your defenses have no new holes when attackers create new strategies and IT environments change. You should conduct routine security audits to identify any vulnerabilities, even after your team has established essential security procedures. Furthermore, you can find potential weak points and improve your attack response strategy by simulating an assault through penetration testing.
-
Use a Proactive Incident Response Plan
Having a solid incident response strategy in place is also crucial. This entails defining precise protocols for locating, handling, and mitigating security events and designating a specific incident response team. For this strategy to continue to work, it has to be evaluated, tested, and modified often.
-
Build a Resilient Disaster Recovery Strategy
Ensuring data security in EHRs also requires implementing a disaster recovery strategy. A disaster recovery plan is an organization’s process for starting again after a calamity, such as a natural disaster or cyberattack. A leading healthcare application development company like SparxIT has the expertise to implement a robust disaster recovery plan.
-
Train Staff to Mitigate Security Risks
Your staff members are crucial in safeguarding EHRs. They must be trained to identify such incidents, including phishing efforts, and notify the appropriate teams. Healthcare organizations must not only adhere to government rules and put in place several levels of protection but also gain and retain the trust of their patients.
Given the increased incidence of data breaches across numerous companies, many patients are legitimately concerned that their information may be stolen or exploited.
-
Partner with a Leading Application Security Services Provider
It is crucial to work with a HIPAA compliance development company with a track record of keeping their EHR system secure. This incorporates a solid dedication to regulatory compliance and data security, as well as frequent security assessments and certifications.
SparxIT guarantees that our products, including the EHR systems, are highly secure and compliant. This is based on our over ten years of expertise in offering healthcare solutions, including clinical research platforms and telehealth solutions.
Building Trust Through Electronic Health Records Security Services
Healthcare organizations may use several best practices to increase patient trust. These include the following.
-
Transparency
Healthcare organizations should be open and honest about their EHR privacy rules. Patients must know how companies safeguard personal data and how it may be accessed or shared.
-
Patient access and control
According to organizations, patients should have authority over their records and be able to access them. Patients should have easy access to their records and control over when to divulge information to the healthcare professionals of their choice.
-
Cybersecurity Training
Cybersecurity training for EHR is essential because human error is the most significant vulnerability to data breaches. According to a study, 88% of data breaches are caused by internal staff mistakes. Cybersecurity training helps you understand privacy regulations, secure medical devices, respond to an incident, realistic phishing simulations, and more.
What Lies Ahead —A Forward-Looking Perspective
Introducing new technologies will change how EHRs are utilized, accessible, and safeguarded. Artificial intelligence (AI) integration could improve productivity by creating progress notes, answering patient inquiries, and automatically generating diagnostic codes. Blockchain—a distributed digital ledger technology—could help safeguard data privacy by constraining access to EHRs.
Standards and rules will probably change. Governmental organizations will adjust guidelines and policies in response to emerging technology and security risks to help guarantee the confidentiality and security of patient data.
For healthcare organizations, managing these developments and safeguarding EHRs may be difficult. Collaborating with external specialists and managed service providers (MSPs) may be advantageous, as they can exchange best practices and relieve IT staff of administrative duties. With the correct partner, you can keep sensitive data safe while maximizing the advantages of EHRs for your company and patients.
Frequently Asked Questions
Q:1 How do application security services for EHR secure patient data?
A: Application security services for EHRs can secure patient data by integrating various methods, such as encryption and multi-factor authentication. As a leading EHR cybersecurity services provider, we also conduct regular security audits, vulnerability assessments, and compliance with industry standards to protect against unauthorized access, data breaches, and compliance violations.
Q:2 How does HIPAA compliance impact EHR security services?
A: HIPAA compliance significantly impacts EHR security solutions by building a framework of regulations and standards that must be fulfilled to protect patient data. This includes the following—
- Security risk assessment
- Workforce Compliance
- Breach notification
- Incident response planning
- Strong data encryption
- Enforcement
Q:3 How can I choose the right healthcare application security solutions provider?
A: When selecting an ideal healthcare application security service, consider factors such as industry experience, compliance certifications (e.g., HIPAA, HITRUST), the range of services offered, client reviews, pricing, and the company’s ability to customize solutions according to your needs.
Q:4 How much does it cost to implement EHR application security?
A: The cost of implementing application security in EHR can vary depending on the organization’s size, security measures, vendor services, and compliance needs.
Here’s the cost analysis–
- Small Practices: $5,000 to $20,000
- Medium-sized Organizations: $20,000 to $100,000
- Large Healthcare Systems: $100,000 to $300,000 or more
These costs cover software solutions, security audits, training, and ongoing maintenance. For accurate pricing details, consult with EHR data protection services.



